SAP Identity Provisioning Service (IPS) plays an important role for user access management in the cloud. SAP IPS is a cloud service provided by SAP on SAP Business Technology Platform. Its task is the provisioning of users and authorizations in cloud and on-premise systems. In this way, SAP IPS offers the possibility of integrating cloud systems into the existing infrastructure. In addition to cloud and on-premise applications, an existing SAP Identity Management (IdM), SAP Identity Access Governance (IAG) or the IdM system of a third-party provider can also be considered as source systems.
Want to automate your user management in the cloud?
User management challenges in the hybrid world
The IT world is increasingly moving toward the cloud. As a rule, companies have hybrid landscapes in place in which they use both on-premise systems and cloud systems. From a technical perspective, hybrid landscapes come with certain challenges for provisioning users and permissions. Cloud systems are outside the corporate network, so the firewall must be overcome to reach them. The multitude of interfaces makes it challenging to address the different systems. Many cloud applications have no authentication mechanism, so authentication is performed against an identity provider. Consequently, it must be ensured that users are not only present in the cloud system, but also in the identity provider behind it.
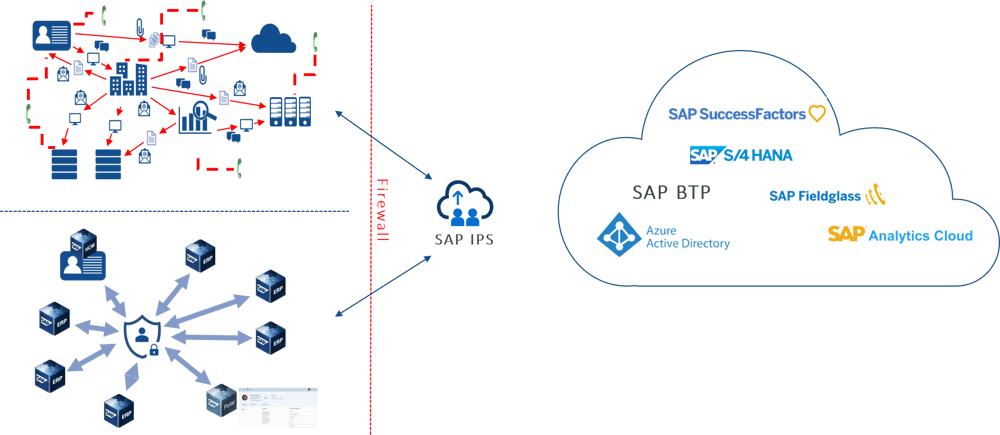
From a technical point of view, the goal should be to map the various identity lifecycle processes with as high a degree of automation as possible. Otherwise, more and more manual effort will be required, since more and more users will have to be authorized to use the cloud systems. Especially if new interfaces are required and additional connectors have to be developed, the effort quickly increases immeasurably without automation.
SAP IPS in stand-alone mode
SAP Identity Provisioning Service is able to automate identity lifecycle processes without an IdM system. Even non-SAP systems can be connected. Two different modes are available for the operation of SAP IPS: the stand-alone mode and the proxy mode. They differ in their functionality and use cases.
In stand-alone mode, SAP IPS acts as a bridge between a source and a target system. Typical source systems are SAP Identity Access Governance (IAG), SAP SuccessFactors or Microsoft Azure Active Directory. The target systems are mostly cloud applications. In principle, however, it is also possible to connect on-premise systems. A source system can be connected to multiple target systems or a target system can be connected to multiple source systems.
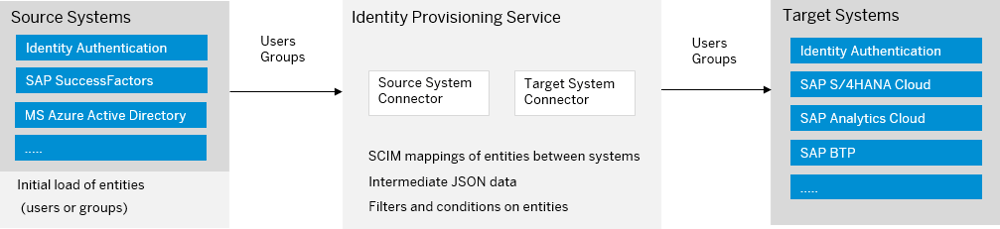
Provisioning from SAP IPS
Users and groups can be written to the target system or systems via SAP IPS. There is a job in SAP IPS to read the data, which can be started manually or scheduled cyclically. Provisioning is done from within SAP IPS. Because data is pulled from the source system and written to the defined target systems, the scenario is also called pull mode. The job can be defined as delta or full read mode. In delta mode, only new or changed records are transferred from the source system and the target system, while full-read mode also transfers unchanged and deleted data.
Example of stand-alone mode
A typical example of stand-alone mode: Microsoft Azure Active Directory serves as the source system and SAP Analytics Cloud as the target system. The first step is to start the “Read data” job in SAP IPS. Users and assignments are then read from Microsoft Azure Active Directory and a data transformation takes place in SAP IPS. The users and assignments are then written to the target system.
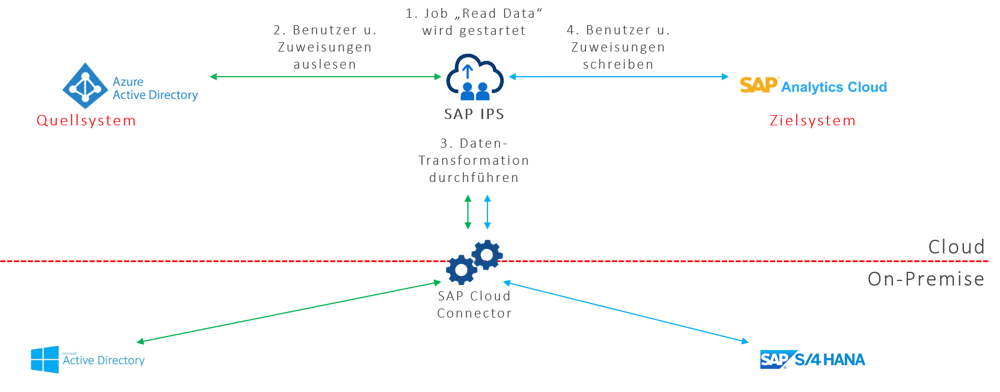
This example is a relatively simple setup, but it can already achieve a certain degree of automation in user management. SAP Cloud Connector can also be used to integrate the on-premise world. It acts as a secure tunnel into the corporate network.
SAP IPS in proxy mode
In proxy mode, SAP IPS serves as middleware and can be addressed via SCIM. Instead of a source system, there is an external consumer, for example SAP Identity Management, SAP Identity Access Governance or a non-SAP system. SAP IPS has the appropriate connectors on board to address the target systems. These are mostly cloud systems. Theoretically, however, it is also possible to connect on-premise systems.
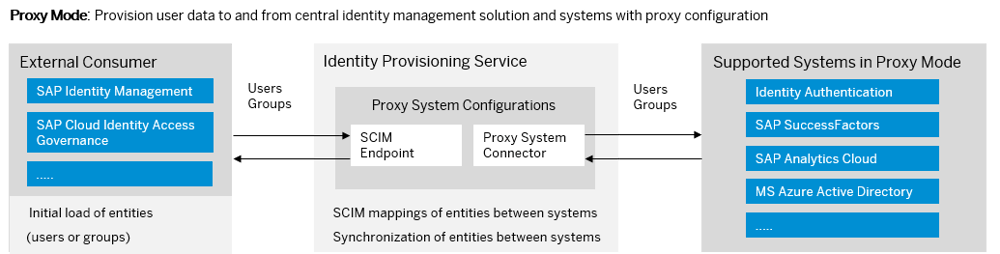
In contrast to stand-alone mode, provisioning in proxy mode is not started from SAP IPS, but triggered from the external consumer system (push mode). The data set is sent to the target system(s) via SAP IPS. The advantage is that individual data records can be provisioned.
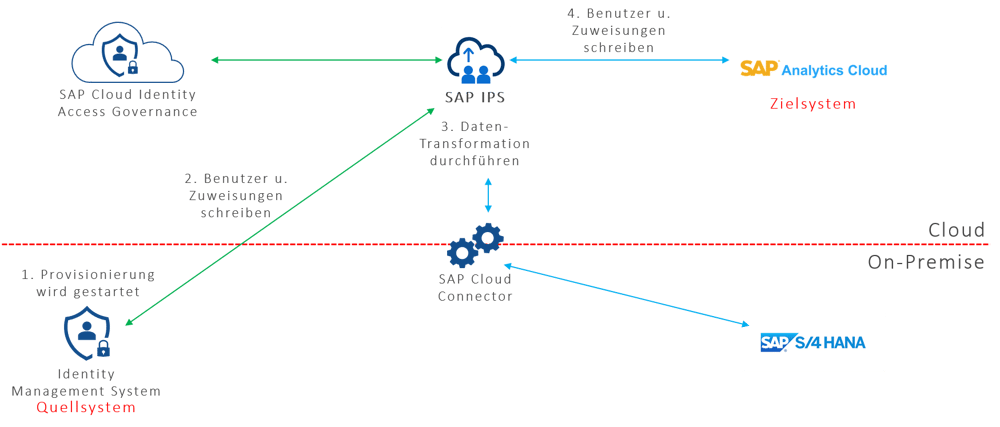
Process flow in proxy mode
The process flow is as follows: A push request takes place from the IdM system: A user is assigned an authorization, then provisioning is to take place, which is started in the IdM system. Users and assignments are sent to SAP IPS, which writes them to SAP Analytics Cloud as the target system. The integration of the on-premise world requires – as in the stand-alone mode – SAP Cloud Connector. Cloud systems can also be considered as source systems for this scenario.
Comparison of stand-alone and proxy mode
Both stand-alone mode and proxy mode have their raison d’être. Stand-alone mode allows data to be read cyclically or manually using the pull method. It offers a simple setup that requires little maintenance. However, not all user lifecycle processes can be optimally mapped with it. Flexibility is relatively low, and complicated use cases cannot be implemented.
The proxy mode allows a more granular handling of users and an efficient administration of authorizations. Another advantage is the better integration into the user lifecycle processes. Due to the significantly more extensive options, SAP IPS in proxy mode also maps more complex setups without any problems.
Conclusion: SAP IPS is not a cloud-based SAP IdM
SAP IPS is used to integrate cloud systems into existing user management processes. Cloud applications in particular can be managed easily and securely with it. The advantages of SAP IPS lie in its standardization and in addressing a single interface in the cloud. After establishing the connection once, numerous target systems can be connected relatively easily.
![IBacademy_Logo_blau[496] IBacademy_Logo_blau[496]](https://www.ibsolution.com/hs-fs/hubfs/IBacademy_Logo_blau%5B496%5D.jpg?width=200&name=IBacademy_Logo_blau%5B496%5D.jpg)




