In complex, hybrid system landscapes composed of multiple platforms, an identity management system provides consistent and secure access to on-premise and cloud resources. The goal is a modular yet integrated identity security solution set.
One Identity Manager is a solution from Quest Software. The American software manufacturer has more than 35 years of experience in cyber security and currently has more than 120 products in its portfolio. One Identity Manager is part of the One Identity solution package “Unified Identity Security”.
Three different types of connectors are available to connect a variety of applications to One Identity Manager.
Native connectors for on-premise solutions
(for example Active Directory, Azure Active Directory, Exchange Online, G Suite, IBM Notes, LDAP, Microsoft Exchange, Oracle E-Business Suite, Microsoft SharePoint, Unix-based target systems, SAP R/3 and SAP S/4HANA, SAP Human Capital Management, SAP Business Intelligence, SAP GRC Access Control)
Starling Connect for cloud applications
(for example SAP SuccessFactors, SAP cloud applications, Atlassian Jira, Atlassian Confluence, Salesforce, Slack, WebEx, Okta, OneLogin)
Custom-developed connectors for customer-specific systems
Automated provisioning of user accounts and permissions
Connection of on-premise and cloud target systems
Certified integration with SAP products
Easily configurable approval and recertification workflows
Reduced workload for IT staff through implementation of Managed Security Services (MSS)
Reports at the touch of a button
Role-based access control
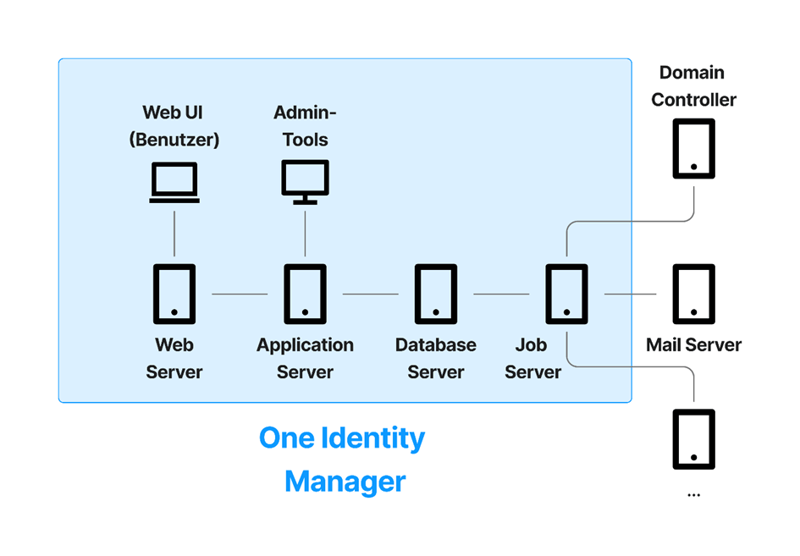
To interact with the system in the course of daily operations, end users use a web UI generated from the backend settings (server-side rendering). In the web portal, users can, for example, order or approve authorizations and resources, manage their own master data, manage their own employees (managers), reset passwords, and much more.
Simply complete the form and submit it. We will get back to you as soon as possible.
Where are the strengths and weaknesses of One Identity in terms of connectivity with SAP applications? In our video, Aydin Tekin takes a closer look at this question using live examples and explains the advantages and disadvantages of the system.

Identity & access management (IAM) deals with the administration and maintenance of user roles and access rights of individual users to applications and cloud services. This primarily involves authenticating and authorizing users according to their role in the company, i.e. establishing their identity and the associated access rights.

Identity Lifecycle Management is part of enterprise security and describes all processes for assigning roles and authorizations − from when an employee joins the company, through changing responsibilities or even department changes, to when he or she leaves.