Simplified SAP Security
Intuitive and dynamic UI
Employee & Manager Self-Service
Intelligent system monitoring
Dynamic real-time reporting
Automated generation of authorization roles
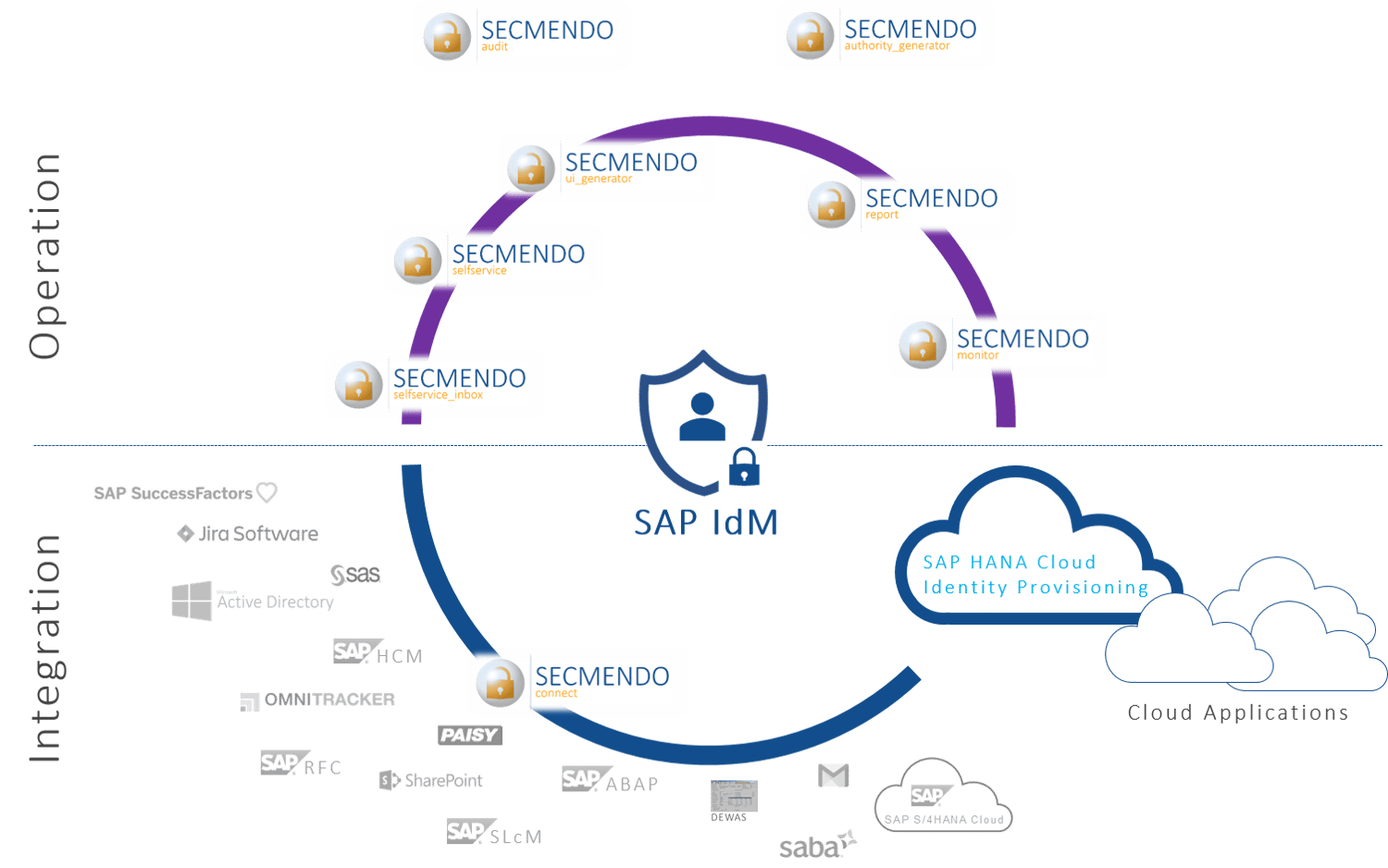
Extension of standard connectivity
System-wide automation
Connection of cloud systems
Proprietary developments based on standard APIs
The tools of the SECMENDO product suite extend the capabilities of existing SAP Identity & Access Management (IAM) solutions. The goals are an improved user experience, enhanced functionality and more efficient processes.

SAP offers the following solutions for maintaining and managing access rights and users:
These solutions, individually or in combination, enable an efficient and compliant operation of target systems. This includes the detection and minimization of risks as well as the process-based provisioning and removal of users and accesses.

Authorizations in SAP systems form the basis for identity & access management. They enable users to access the applications they need to perform their tasks. Since functional and organizational requirements are subject to change, SAP authorizations must be regularly checked and reworked. This is the only way to ensure that processes are mapped securely and completely correctly from a technical point of view.
In order to identify and minimize risks in authorizations and to assign them correctly via the SAP user lifecycle, the use of supporting solutions from identity & access management is recommended.

Clean up with historically grown roles and authorizations
Tailored roles and authorizations on a tap
Increased employee productivity and relief for the IT department
User-friendly interfaces for managing roles and permissions in just 5 minutes
User-friendly and fast processing of work items from the UWL
24/7 monitoring of your SAP IdM landscape and provisioning processes
Audits and reports on a tap
System-wide automation, on-premise and in the cloud
Real-time validation of user entries

Identity lifecycle management is part of enterprise security and describes all processes for assigning roles and authorizations − from when an employee joins the company, through changing responsibilities or even department changes, to when he or she leaves.

Identity & Access Management solutions, individually or in combination, enable efficient and compliant operation of target systems. This includes the detection and minimization of risks as well as the process-based provisioning and removal of users and accesses.

Authorizations in SAP systems grant users access to the applications they need to perform their activities. In order to map the processes securely and correctly, SAP authorizations must be subject to regular control and post-processing.
Simply complete the form and submit it. We will get back to you as soon as possible.